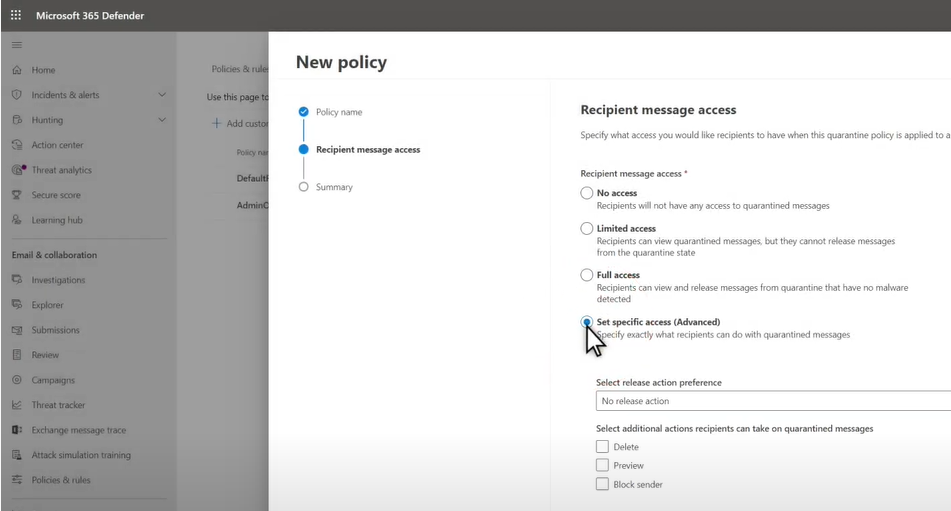
Microsoft is updating Defender for Office 365 soon to help protect customers from embedded email threats while they are previewing quarantined emails. Microsoft is rolling out more quarantine management features that will help allow IT professionals and end users to better investigate quarantined emails:
- Quarantine folder policy and user release request workflow
- Customer organization branding
- Streamlined email submission from the quarantine portal
- Robust release of bulk quarantined emails
- Secured preview of quarantined emails
- Quarantine support for shared mailboxes
Microsoft Defender for Office 365 (previously Office 365 Advanced Threat Protection) provides world-class protection for enterprise email accounts against threats that include business email compromise and credential phishing. They even have some features that help with automated attack remediation.
These new enhancements should help limit risk to unwanted or malicious content by providing additional security controls to help block embedded threats to help prevent threat actors from knowing their intended victim has loaded an image or other embedded content in the quarantine preview.
“We’re changing the way users preview quarantined messages to provide additional security against embedded threats,” Microsoft explains on the Microsoft 365 roadmap. The idea is to provide some additional controls when previewing an email to make sure the threats are contained and the sender is less likely to know you have contained the suspicious email. With this change some components in quarantined messages will be distorted and not displayed by default. To see the full contents of the message, users can choose to reveal the full message.”
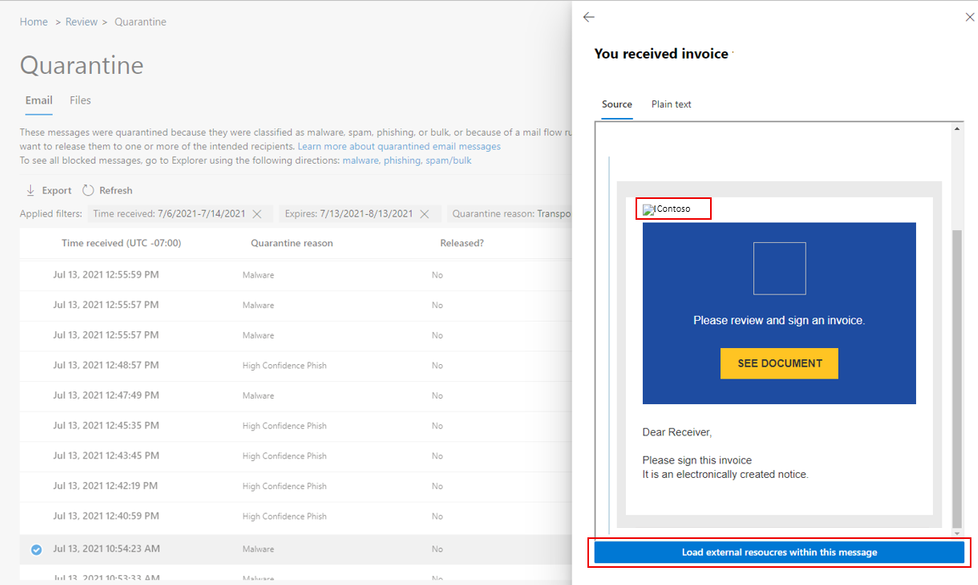
Other new features will allow for more control over quarantine items, release workflow options, corporate branding, and support for shared mailboxes.
Microsoft also plans on adding more intelligence around what kinds of attacks are targeting your business and options around how to deal with ongoing threats.